Biometry: Difference between revisions
(Course of Action) |
|||
| (11 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
=Introduction= |
|||
'''Biometry''' is the statistical analysis of biological observations and phenomena([http://www.m-w.com/cgi-bin/dictionary?va=biometry]). Biometry is coupled with the measurement of '''biometric'''s: measurable, physical characteristics or personal behavioral traits used to recognize the identity, or verify the claimed identity of a person. |
|||
In the context of [[Security Engineering]] there are traditionally two links between a person and her identity: |
|||
* Something I know ([[Passwords]]) |
|||
* Something I have (tokens) |
|||
With biometry it should —in theory— be possible to establish a third link: |
|||
* Something I am |
|||
Therefore biometric systems can play an important role in [[Wikipedia:Authentication|authenticating]] a user. |
|||
=Overview= |
|||
*Broad Overview on Biometric Criteria |
|||
*Facial recognition |
|||
**Use, Scenario, Features |
|||
**General course |
|||
**Approaches |
|||
**Summary |
|||
*Insights on Fingerprints |
|||
**Features |
|||
**Acquisition |
|||
**Recognition |
|||
**Demonstration |
|||
**Problems |
|||
==Modes of Operation== |
|||
=Short Introduction= |
|||
Two different modes must be distinguished: |
|||
*I biometry: the statistical analysis of biological |
|||
; Identification : “Who is it?” |
|||
observations and phenomena (Merriam-Webster |
|||
; Authentication : “Is it her?” |
|||
Online Dictionary) |
|||
*I biometric: a measurable, physical characteristic or |
|||
personal behavioral trait used to recognize the |
|||
identity, or verify the claimed identity of a person |
|||
*I Three levels: |
|||
**1. I know something (passwords) |
|||
**2. I have something (tokens) |
|||
**3. I am something (biometry) |
|||
Not all biometric systems can feasibly operate in both modes. For example if it takes a given system 1 second to authenticate a given user this would generally be deemed acceptable. If however the same system should be used to identify a user in a database of 10.000 users by simply trying the authentication on each database record in turn this would take 10.000 seconds or more than 2 hours and 46 minutes. In almost all but very few scenarios this will be completely unacceptable. |
|||
=Classification= |
|||
Two diffent modes must be distinguished: |
|||
*Identification “Who is it?” |
|||
*Authentication “Is it her?” |
|||
On the other hand some identification systems simply return the record that best matches the query. So when the person that is to be identified is not part of the database some —more or less— random record is returned. For that reason a common design for an identification system is to chain a '''indexing''' system which returns the <math>n</math> best matches and an authentication system. |
|||
=Quality indices= |
|||
False Rejection Rate (frr) |
|||
*Rate of authentication attempts from legitimate users that are rejected. |
|||
False Acceptance Rate (far) |
|||
*Rate of authentication attemps from illegitimate users (e.g. attackers) that are accepted. |
|||
Equal Error Rate (eer) |
|||
*The eer equals the far and frr when the system is configured so that far = frr. |
|||
Failure to Enroll Rate (fer) |
|||
*Rate of users that can’t enroll into the system at all. |
|||
==Course of Action== |
|||
=Hand geometry= |
|||
Being [[Wikipedia:Pattern recognition|pattern recognition]] systems most biometric systems operate by first reducing the input (oftentimes an image) to a small set of features. Use of this set is twofold: |
|||
*Hand is placed on a reflective surface |
|||
# During the enrollment procedure, e.g. when the user is first introduced to the system, the set is transformed into a reference template which is then saved in a database. It is common to form the reference template by taking several measurements of the biometric and then averaging them. |
|||
*Hand is lit by some light source (e.g. bright LED) |
|||
# During regular use in identification or authentication systems the set of features is compared against the reference template(s) from the database. |
|||
*a camera and some mirrors are used to gather images of several parts of the hand from several angles |
|||
*the template consists of measurements extracted from the image |
|||
<center>[[Image:Biometric_flow_small.png|Typical biometric data flow for enrollment and authentication.]]<br> |
|||
=Retina scanning= |
|||
Typical flow of biometric data for the enrollment and authentication in an authentication system. There is also a [[:Image:Biometric_flow.png|larger version]] available.</center> |
|||
*was available before iris scanning |
|||
*good (e.g. low) far |
|||
*a low intensity light source is used to scan the vascular pattern |
|||
==Quality indices== |
|||
=Other techniques= |
|||
Several quality indices are defined to compare different systems: |
|||
*voice verification |
|||
; False Rejection Rate (FRR) : This is the rate of authentication attempts from legitimate users that are rejected. |
|||
*signature verification |
|||
; False Acceptance Rate (FAR) : This is the rate of authentication attempts from illegitimate users (e.g. attackers) that are accepted. |
|||
*vein pattern scanning |
|||
; Equal Error Rate (EER) : This is the false acceptance rate (or the false rejection rate) when the system is set up so that the FRR equals the FAR. |
|||
*scent |
|||
; Failure to Enroll Rate (FER) : This is the rate of users that can't enroll into the system at all. |
|||
*keystroke patterns |
|||
Quite naturally the first three only apply to authentication systems. |
|||
In most real world systems a high FAR is worse than a high FRR: When a legitimate user is rejected she simply tries again causing only a slight comfort loss. Accepting a illegitimate user, though, compromises the system and would usually lead to a loss of whatever the system was meant to protect. |
|||
=Use= |
|||
*artifical intelligence |
|||
**autonomic systems should interact with human, recognize and interpret |
|||
**facial expressions as essential component |
|||
*civil authentification |
|||
**drivers licence, credit cards, access |
|||
**inconspicuous, good acceptance by users expected |
|||
**question: reliability, frontiers (twins) |
|||
*identification in delinquency (crime) |
|||
**cameras, automatical identification of suspects |
|||
**support search for missing persons |
|||
As different environments have different requirements regarding the security of the system and the convenience of the users most systems have some sort of adjustment possibility, e.g. a threshold value for the number of matches features. This can usually be set to trade off a higher FAR in favor of a lower FRR or vice versa. To aid in comparison of biometric systems one then uses the equal error rate: The adjustment is set so that FRR=FAR which then gives the EER. The EER of different systems can then be compared. (In reality mostly no one would use a system configured this way, as detailed above.) |
|||
=Scenario= |
|||
*controlled environment |
|||
**uniform head position, cooperative users, good |
|||
image quality |
|||
*uncontrolled environment |
|||
**face has to be found, position, orientation, size, illumination (shadows), bakground, are variable and have to be compensated |
|||
**facial expression (laughing) has big influence |
|||
**face partially hidden, beard, hairstyle, glasses, hat can hide parts of the facial information |
|||
**injuries, holiday, age change the face |
|||
<center>[[Image:Frrfar.png|The graph shows some overly idealistic FRR and FAR curves depending on some sort of threshold and the EER point.]]<br> |
|||
FRR and FAR curves and the point of EER.</center> |
|||
A fundamental index in all systems that employ some sort of database of reference templates is the Failure to Enroll Rate, e.g. the rate of users that can't enroll into the system. In these systems a reference dataset must be aquired from each user prior to any operations (enrollment). This operation can fail, for example due to intrinsic properties of the person trying to enroll. E.g. it would be impossible to enroll into a system based on hand geometries for a person that has no hands. Similarly a mute person won't be able to enroll into a speech verification system, etc. And what use is a system with the best possible EER if two thirds of the prospective users can't enroll? |
|||
=Definition of Features= |
|||
*before identification |
|||
**face has to be found and separated from the background |
|||
**separating background and illumination are big problems |
|||
*manual definition of features |
|||
*calculation of features often not reliable |
|||
*amount of manually defined features too small to separate different people |
|||
*immense variety of features has to be expected |
|||
=Overview on Biometric Criteria= |
|||
There are several parts of the human anatomy that are sufficiently unique and stable during a long time and therefore suited for use as biometric criteria. The most common are: |
|||
* [[Fingerprint Matching|fingerprints]] |
|||
* [[Facial Recognition|faces]] |
|||
* [[Hand Geometry|hands]] |
|||
* [[Iris Scanning|irides]] |
|||
* [[Retina Scanning|retinae]] |
|||
* vein patterns |
|||
There are also some personal behaviors or similar habits that can be used as biometrics: |
|||
=Generating Templates= |
|||
* signatures |
|||
comparison |
|||
* voices |
|||
*different procedures are used |
|||
* keystroke patterns |
|||
*general: |
|||
**byte-comparison of two templates |
|||
**use of algorithms (vector operations) |
|||
**grade of similarity |
|||
**if within tolerance then identical |
|||
*algorithms: |
|||
**template matching |
|||
**elastical bunch graph matching |
|||
**geometrical features |
|||
**“eigenfaces” |
|||
=References= |
|||
*Ashbourn, J. (2000). Biometrics: Advanced identity verification: The complete guide. London: Springer. |
|||
*Bhanu, B., & Tan, X. (2004). Computational algorithms for fingerprint recognition. Boston / Dordrecht/ London: Kluwer Academic Publishers. |
|||
*Thalheim, L., Krissler, J., & Ziegler, P.-M. (2002). Koerperkontrolle [Body check]. In c’t 11/2002. Hannover: Heise. (English version at [http://www.heise.de/ct/english/02/11/114/ heise online]) |
|||
Also see the slides at [http://www.informatik.hu-berlin.de/~ploetz/biometry] (PDF format, 5.5 MB). |
|||
=Template Matching= |
|||
*similarity between image and template is calculated |
|||
*template: for whole face or parts (eye, mouth, nose) |
|||
*unknown face is compared with all that were saved |
|||
*problems |
|||
**mask has to match for a lot of faces |
|||
**a lot of time necessary, quality depends from mask |
|||
=Elastic Bunch Graph Matching= |
|||
*Labeled Graph (LG): nodes at certain parts of face (nose, mouth,..); universal face graph |
|||
*Bunch Graph (BG): every node gets different features as a subgraph (specializing the LG) |
|||
*Facial Recognition: find face, find certain parts, calculate BG and compare graphs |
|||
*save useful variation |
|||
=Deformable Templates= |
|||
*analyze face with geometrical figures |
|||
*alignment, shape, size, but also especially the position of the elements to each other |
|||
*samples (templates) are adapted to concrete face |
|||
*notes |
|||
**Templates comparable with LG; has to be adapted to concrete face |
|||
**Extraction of edges necessary; not very reliable |
|||
=Recognition with geometrical features= |
|||
*geometrical features are extracted from face |
|||
**simple extraction, difficult classification |
|||
*possible features |
|||
**horizontal and vertical projection of parts (eyes,nose, . . .) |
|||
**position, central point, width, thickness, radius of parts of the face |
|||
="Eigenfaces"= |
|||
*beginning: amount of faces: |
|||
**1. mean value calculation of the sample faces |
|||
**2. mean value from step 1 subtracted from every sample face |
|||
**3. “Kovarianzmatrix” calculation of normalized images from step 2 |
|||
**4. mathematical procedure gives optimal base of Eigenfaces |
|||
*base for effizient facial recognition / data compression |
|||
*condition: all faces to be recognized were trained before and represented: (calculation of “Eigenfaces-Base”) |
|||
*recognition of an image |
|||
**projection into “Eigenfaces-Base” |
|||
**Comparison of resulting values |
|||
**assign to registered face (person) thats value is next to |
|||
*problem: classify unknown faces |
|||
=3D Recognition= |
|||
*Features: |
|||
**developed in israel |
|||
**further development at Siemens/Munich |
|||
**“contoured face mask” is built up |
|||
**superior quality compared with 2D images |
|||
**very fast and reliable |
|||
**does not care about the position of the face |
|||
*How it works: |
|||
**project coloured lines |
|||
**at varying heights no straight lines |
|||
**position of each pixel is calculated to geometric data |
|||
**(3D Image at precision of 0.2 x 0.2 x 0.2mm within 40 ms) |
|||
**image analysed by using classical recognition methods |
|||
**! more secure |
|||
**! impossible to cheat the system by placing a photo in front of the camera |
|||
=Summary= |
|||
*Evaluation and Comparison |
|||
**feature based approaches |
|||
***can handle different orientations of faces |
|||
***manual definition of features |
|||
***automatical extraction of features / classification not very reliable |
|||
**appearance based approaches |
|||
***for every view separate image of the person is necessary |
|||
***simple to realize, automatical feature extraction |
|||
=Insights on Fingerprints= |
|||
*Features found on fingers |
|||
*Acquisition of fingerprints |
|||
*Recognition of fingerprints |
|||
*Some demonstration |
|||
*Problems of fingerprints |
|||
=Classification of fingerprints= |
|||
In the Henry system of fingerprint classification there are five different classes of fingerprints: |
|||
*Right Loop |
|||
*Left Loop |
|||
*Whorl |
|||
*Arch |
|||
*Tented Arch |
|||
The frequency of each class seems to vary with ethnic origin: Europeans have mostly loops, Pygmies and African bush men mostly have archs and Orientals have plenty of whorls. |
|||
=Minutiae= |
|||
Different types of minutiae: |
|||
*endings |
|||
*bifurcations |
|||
=Devices= |
|||
There’s a plethora of different sensor types: |
|||
*capacitive |
|||
*optical (several principles) |
|||
*thermic |
|||
*ultrasonic |
|||
*pressure |
|||
Acquisition methodology: |
|||
touching vs. sweeping |
|||
=typical extraction flow= |
|||
*fingerprint image |
|||
*binarization |
|||
*thinning |
|||
*minutiae extraction |
|||
*post processing |
|||
*minutiae |
|||
Latest revision as of 06:50, 23 February 2005
Introduction
Biometry is the statistical analysis of biological observations and phenomena([1]). Biometry is coupled with the measurement of biometrics: measurable, physical characteristics or personal behavioral traits used to recognize the identity, or verify the claimed identity of a person.
In the context of Security Engineering there are traditionally two links between a person and her identity:
- Something I know (Passwords)
- Something I have (tokens)
With biometry it should —in theory— be possible to establish a third link:
- Something I am
Therefore biometric systems can play an important role in authenticating a user.
Modes of Operation
Two different modes must be distinguished:
- Identification
- “Who is it?”
- Authentication
- “Is it her?”
Not all biometric systems can feasibly operate in both modes. For example if it takes a given system 1 second to authenticate a given user this would generally be deemed acceptable. If however the same system should be used to identify a user in a database of 10.000 users by simply trying the authentication on each database record in turn this would take 10.000 seconds or more than 2 hours and 46 minutes. In almost all but very few scenarios this will be completely unacceptable.
On the other hand some identification systems simply return the record that best matches the query. So when the person that is to be identified is not part of the database some —more or less— random record is returned. For that reason a common design for an identification system is to chain a indexing system which returns the best matches and an authentication system.
Course of Action
Being pattern recognition systems most biometric systems operate by first reducing the input (oftentimes an image) to a small set of features. Use of this set is twofold:
- During the enrollment procedure, e.g. when the user is first introduced to the system, the set is transformed into a reference template which is then saved in a database. It is common to form the reference template by taking several measurements of the biometric and then averaging them.
- During regular use in identification or authentication systems the set of features is compared against the reference template(s) from the database.
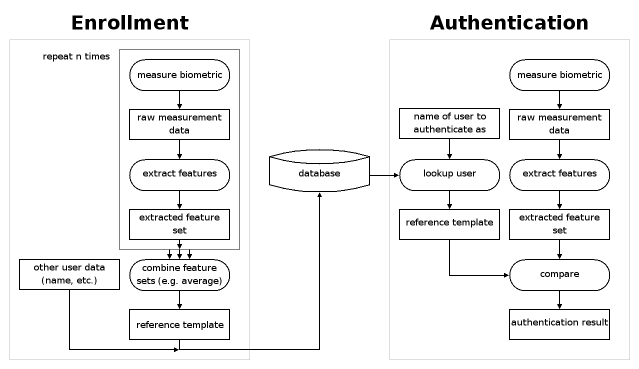
Typical flow of biometric data for the enrollment and authentication in an authentication system. There is also a larger version available.
Quality indices
Several quality indices are defined to compare different systems:
- False Rejection Rate (FRR)
- This is the rate of authentication attempts from legitimate users that are rejected.
- False Acceptance Rate (FAR)
- This is the rate of authentication attempts from illegitimate users (e.g. attackers) that are accepted.
- Equal Error Rate (EER)
- This is the false acceptance rate (or the false rejection rate) when the system is set up so that the FRR equals the FAR.
- Failure to Enroll Rate (FER)
- This is the rate of users that can't enroll into the system at all.
Quite naturally the first three only apply to authentication systems.
In most real world systems a high FAR is worse than a high FRR: When a legitimate user is rejected she simply tries again causing only a slight comfort loss. Accepting a illegitimate user, though, compromises the system and would usually lead to a loss of whatever the system was meant to protect.
As different environments have different requirements regarding the security of the system and the convenience of the users most systems have some sort of adjustment possibility, e.g. a threshold value for the number of matches features. This can usually be set to trade off a higher FAR in favor of a lower FRR or vice versa. To aid in comparison of biometric systems one then uses the equal error rate: The adjustment is set so that FRR=FAR which then gives the EER. The EER of different systems can then be compared. (In reality mostly no one would use a system configured this way, as detailed above.)

FRR and FAR curves and the point of EER.
A fundamental index in all systems that employ some sort of database of reference templates is the Failure to Enroll Rate, e.g. the rate of users that can't enroll into the system. In these systems a reference dataset must be aquired from each user prior to any operations (enrollment). This operation can fail, for example due to intrinsic properties of the person trying to enroll. E.g. it would be impossible to enroll into a system based on hand geometries for a person that has no hands. Similarly a mute person won't be able to enroll into a speech verification system, etc. And what use is a system with the best possible EER if two thirds of the prospective users can't enroll?
Overview on Biometric Criteria
There are several parts of the human anatomy that are sufficiently unique and stable during a long time and therefore suited for use as biometric criteria. The most common are:
- fingerprints
- faces
- hands
- irides
- retinae
- vein patterns
There are also some personal behaviors or similar habits that can be used as biometrics:
- signatures
- voices
- keystroke patterns
References
- Ashbourn, J. (2000). Biometrics: Advanced identity verification: The complete guide. London: Springer.
- Bhanu, B., & Tan, X. (2004). Computational algorithms for fingerprint recognition. Boston / Dordrecht/ London: Kluwer Academic Publishers.
- Thalheim, L., Krissler, J., & Ziegler, P.-M. (2002). Koerperkontrolle [Body check]. In c’t 11/2002. Hannover: Heise. (English version at heise online)
Also see the slides at [2] (PDF format, 5.5 MB).
