BitLocker
Bitlocker Drive Encryption is a data protection feature integrated in Windows Vista Ultimate and Windows Vista Enterprise, which was designed to protect the data through encrypting the entire system volume. For the encryption the Advanced Encryption Standard (AES) algorithm in Cipher-block chaining is usedAES-CBC, as well as the Elephant-Diffuser which provides more security that is not provided through AES alone. Further more Bitlocker, on computers with a compatible Trusted Platform Module (TPM), provides a way to validate the integrity of the startup components of the system before starting vista itself.
AES-CBC
The AES is a widely used symmetric block cipher that works on fixed blocks, the block size is always a multiple of 16 bytes so no padding is necessary. BitLocker provides AES key size of either 128 Bits or 256 bits depending on the users choosing.
CBC – Cipher-Block chaining mode was invented by IBM in 1976, each block of plaintext is XORed with the previous ciphertext block before beeing encrypted, where the IV(initiation vector) under BitLocker is selected through a function that maps each sector number into a unique 16-byte value. This way, each ciphertext block depends on the previous blocks which have been proccesed, so if any changes are made to a cipherblock every following block of plaintext is effected.
The Diffuser
The Diffuser is a feature to secure against cipher attacks, through writing the data in a more randomly order on the hard disk instead a sequential order. This way, the probability that manipulated ciphertext will translate into none random output is decreased. For example an attacker could manipulate ciphertext in a way that causes crashing or stopping of processes inside the system for further exploits, through watching cipher text changes during boot the attacker could exploit those sectors through changing them and look at the effects. So if the attacker can create meaningful plaintext changes through cipher text changing, that could lead to future security holes. This is where the Diffuser steps in, through putting the data on the disk in a kind of random way, the same plaintext does not create the same ciphertext on the hard disk, which makes ciphertext attacks harder. (work in progress)
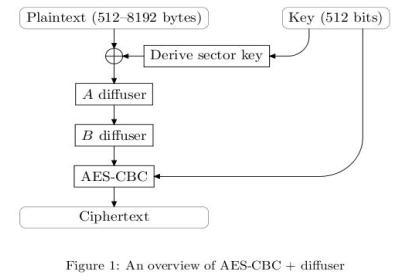
AES-CBC+Diffuser
This is an overview of the operations taking place in the BitLocker encryption process, taken out of the Ferguson paper from 2006. The encryption process encrypts a block of a size between 512-8192 bytes, on any power of two. First the plaintext is XORed with a sector key, secondly it runs through 2 un-keyed diffusers and finally the plaintext is encrypted with AES-CBC. The sector key and the AES key are independent keys, where the sector key is a 128 or 256 bit key for the specific sector, so that each sector has different ciphertext even if the same plaintext is actually used. Both keys (256+256) are together a 512 key where smaller keys (128) are possible by leaving unused bits.
Performance
Usually encryption affects the system performance, with an estimated loss of 20%. Microsoft set up special performance requirements for BitLocker to keep the loss as small as possible. The requirements where calculated on the performances of typical machines, the most systems today run at 3 GHz P4 CPU with hard disk speed around 50 MB/s, which leaves 60 clock cycles per byte while the processor waits for an requested byte. Also there are the laptops with slower systems typically at 1 GHz with hard disk nearly at 50 MB/s, which means that on such a system there are only 30-40 clock cycles per byte. To ensure that the performance loss is as small as possible the decryption/encryption process must be as leas as fast as the peak data rate of the disk, meaning that the algorithm used has only 30 clock cycles per byte, BitLocker meets just that requirement, the 128 bit AES-CBC algorithem implementation needs 20 cycles and the Diffuser provided is at 10 cycles per byte, this leaves the over all encryption process of BitLocker at 30 clock cycles. On test-systems BitLocker with AES-CBC+Diffuser had only 5% performance loss.
Requirement and installation
BitLocker is only included in the Windows Vista Ultimate and Enterprise edition, also u need at least a 50 GB NTFS system partition (C:), a 1,5 GB NTFS boot partition where the OS boots from that will not be encrypted. For the use with a Trusted Platform Module(TPM) a TPM compatible BIOS is needed and the TPM must be v1.2 or later, without TPM BitLocker can be configured with a USB device or smart/card. The installation of BitLocker is not chained to the installation of the OS, BitLocker can be installed and configured after the installation of VISTA with the BitLocker Drive Preparation Tool that is available on the Microsoft site.
BitLocker and TPM
The TPM(Trusted Platform Module) is a microchip designed to provide basic security functions as specified by the Trusted Computing Group (TCG), it provides a lot of functions for static authentication of the platform. BitLocker uses only a handful of the TPM capabilities, that involve keys. Each TPM has its own master key, which is called the Storage Root Key (SRK), this key is never revealed to any other software or hardware components, it is only used inside the TPM. This SRK is used to encrypt any key given to the TPM(which is called “wrapping”), a key given to the TPM can be tied to a specific hardware or software conditions (called “sealing”), so that the TPM only gives out that key if the system conditions are correct. By sealing a key, TPM creates a snapshot of the configurations of the system, as well as file hashes on files that are important for the systems boot process and stores them in the Platform Configuration Registry (PCR) and only if the system is identical to the snapshot in the PCR the “sealed” key is released. This way BitLocker uses TPM so ensure that the system has not been tampered with.
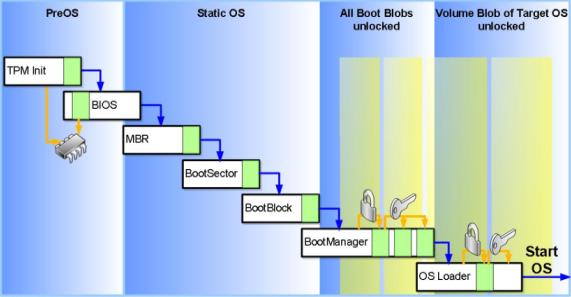
Bootprocess
(The above chart is copied from a Powerpoint presentation on the Microsoft's website)
The chart shows the following process: at power-up the processor starts running the BIOS from ROM. The first part of the BIOS cannot be modified. This part extends the BIOS PCR with the entire BIOS code and proceeds with the rest of the BIOS startup. After BIOS initialization the BIOS reads the Master Boot Record (MBR) of the hard disk, extends the boot sector PCR with the sector’s data, and then executes the code in the boot sector. The boot sequence of a PC contains several more iterations, but in each case the newly-loaded code is first measured using an extend function before it is executed. These functions do not interfere with the boot process of another operating system. Other operating systems can boot normally; but the TPM PCRs will have a different value. The PCRs merely report what software was run during the boot process
References and weblinks
| • http://www.microsoft.com/technet/security/guidance/clientsecurity/dataencryption/analysis/4e6ce820-fcac-495a-9f23-73d65d846638.mspx/ |
| • http://windowshelp.microsoft.com/Windows/en-US/help/6035e2fd-ee50-4b74-9bfb-6c27bb6bf2201033.mspx |
| • http://articles.techrepublic.com.com/5100-10878_11-6162979.html |
| • http://en.wikipedia.org/wiki/Block_cipher_modes_of_operation |
| • “AES-CBC + Elephant diffuser A Disk Encryption Algorithm for Windows Vista“, Niels Ferguson Microsoft - 2006 |