Security in E-Commerce Systems: Difference between revisions
Jump to navigation
Jump to search
No edit summary |
|||
| (4 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
==Introduction== |
|||
In e-Commerce Systems two things must be guaranteed: |
|||
* The communication partner must in fact be the person he says he is. |
|||
* The communication must be secure. |
|||
The first demand can be fulfilled by an authentication with certificates.<br> |
|||
And the second demand can be fulfilled by encryption with SSL. |
|||
==Technologie== |
==Technologie== |
||
The most used protection technologie in e-Commerce Systems is PKI (Public Key Infrastructure). |
The most used protection technologie in e-Commerce Systems is PKI (Public Key Infrastructure). |
||
| Line 17: | Line 26: | ||
* Prolongation/Renewal/Withdrawal |
* Prolongation/Renewal/Withdrawal |
||
* Validation, Cross Certification |
* Validation, Cross Certification |
||
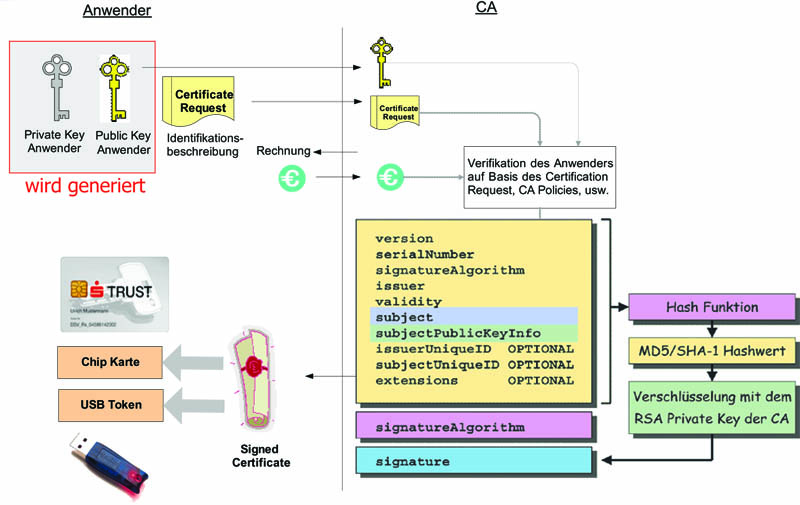
At the following Picture you can see how a signed certificate is generated. |
|||
[[Image:Signed_certificate_creation.jpg|left|none|thumb|700px|Way of origin of a signed Certificate]] |
|||
For more information about PKI and Certificates see also: [[Digital Certificates and Digital Signatures]]. |
For more information about PKI and Certificates see also: [[Digital Certificates and Digital Signatures]]. |
||
==Weak Points== |
==Weak Points== |
||
The most frequent weak points in e-Commerce Systems are: |
The most frequent weak points in e-Commerce Systems are: |
||
* too short and too simple passwords |
* too short and too simple [[passwords]] |
||
* weak encryption (with too short keys) |
* weak encryption (with too short keys) |
||
* careless use with passwords and access data |
* careless use with [[passwords]] and access data |
||
Latest revision as of 22:34, 18 January 2005
Introduction
In e-Commerce Systems two things must be guaranteed:
- The communication partner must in fact be the person he says he is.
- The communication must be secure.
The first demand can be fulfilled by an authentication with certificates.
And the second demand can be fulfilled by encryption with SSL.
Technologie
The most used protection technologie in e-Commerce Systems is PKI (Public Key Infrastructure). A PKI consists of a Registration Authority (RA) and a Certification Authority (CA).
Tasks of the RA:
- Reception of certificate requests
- Authentication of persons and authorities
- Verification of data
- communicates confidentially with the CA
- Distribution and verification of certificates
- direct interface to the customer
Tasks of the CA:
- Generation of certificates
- Prolongation/Renewal/Withdrawal
- Validation, Cross Certification
At the following Picture you can see how a signed certificate is generated.
For more information about PKI and Certificates see also: Digital Certificates and Digital Signatures.
Weak Points
The most frequent weak points in e-Commerce Systems are: