NAT Traversal: Difference between revisions
| Line 106: | Line 106: | ||
<td> |
<td> |
||
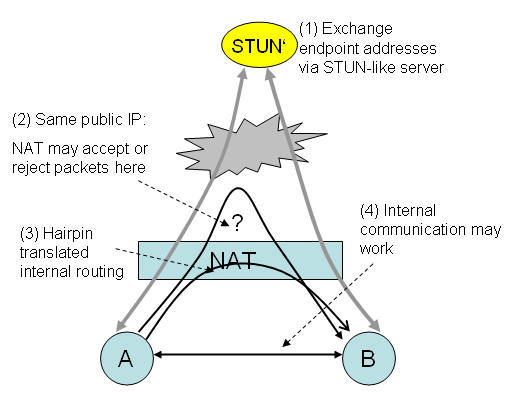
Since hole punching works for two clients behind different NATs, we now focus on a special case when two clients are behind the same NAT. Remember the restrictions to STUN protocol: the clients may find out they are behind the same NAT, but they actually do not know whether they are in the same private network (--> cascaded NATs).<br/> |
Since hole punching works for two clients behind different NATs, we now focus on a special case when two clients are behind the same NAT. Remember the restrictions to STUN protocol: the clients may find out they are behind the same NAT, but they actually do not know whether they are in the same private network (--> cascaded NATs).<br/> |
||
Now the clients can try normal hole punching. If this works or not depends on the NAT's ability of doing so-called hairpin translation. Since clients from private network try to connect to NAT's public |
Now the clients can try normal hole punching. If this works or not depends on the NAT's ability of doing so-called hairpin translation. Since clients from private network try to connect to NAT's public addresses, the NAT may deny this communication. In the best case, the NAT will translate the request internally by opening a direct route to the NATed client. Also possible were to send the request to the internet and receive it like a normal request, but this is inefficient.<br/> |
||
To achieve the best performance, clients may try to connect to the private address obtained from STUN server. If the clients are located in the same subnet, this will work. By the way, this is a possible method for traversing symmetric NATs. |
To achieve the best performance, clients may try to connect to the private address obtained from STUN server. If the clients are located in the same subnet, this will work. By the way, this is a possible method for traversing symmetric NATs. |
||
</td> |
</td> |
||
Revision as of 11:15, 11 February 2006
Note: work in progress
Overview
NAT (Network Address Translation) is widely used to connect private networks to the internet. The main idea is to map several private IP addresses to only one public IP address. Having in mind that P2P network clients should be able to communicate with each other, one basic question comes into mind: how can internet hosts communicate with a host in a private network? We will first have a look at NAT itself and problems it brings. Then, we show how to traverse NATs by either changing router's configuration or by using other tricks.
Network Address Translation
A network address is simply the IP address ( + Port number for UDP/TCP). A NAT router receives an incoming IP packet, saves the address in its NAT table, rewrites sender address to one of its public addresses and sends the packet to the destination address. Now, the NAT router accepts incoming packets on this public address (NAT endpoint). These packets are forwarded to the private host. The most important facts are:
- The mapping depends on the sender's port number. If the private host uses two different outgoing port numbers, the NAT endpoints will differ.
- The private host has to send first. Otherwise no incoming packets will be forwarded to the private host.
- The client does not know all that...
The behavior of the NAT router is not standardized. The only thing that works with every NAT router is simple request and answer. That means the remote host answers a request using the port number the client used for its request. Some NATs allow replies from other ports or even hosts, some use different endpoint mappings for every session.
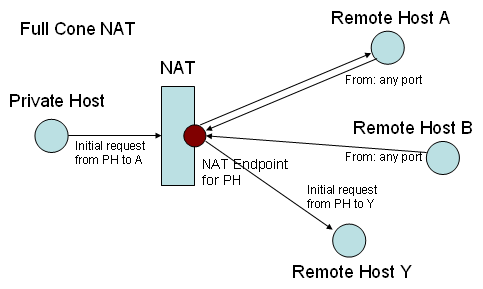
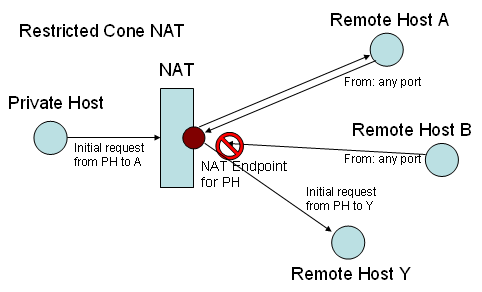
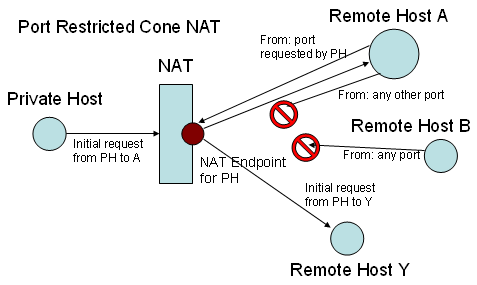
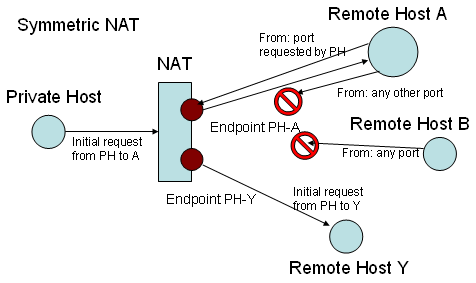
According to their behavior, NATs can be classified into four types:
- Full Cone
- Restricted Cone
- Port Restricted Cone
- Symmetric
Router configuration
Port forwarding
UPnP
STUN
TURN
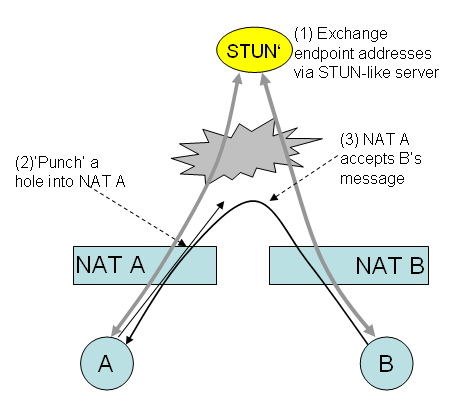
Hole punching
Conclusion: hole punching is not a cure-all for traversing NATs, but works fine for Cone-type NATs. Symmetric NATs cannot be traversed by using these simple methods.
Hairpin translation is a special case for hole punching and may allow direct communication for clients behind the same symmetric NAT. If all that does not work, the fallback strategy is to use relayed connections using the TURN protocol.