Wired Equivalent Privacy
IEEE 802.11 Standard
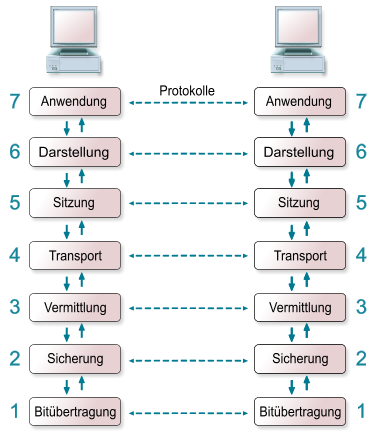
The IEEE 802.11 standard that was published 1997 by the Institute of Electrical and Electronics Engineers (IEEE). The standard specifies the two lowest layers of the OSI (Open System Interconnection) model for local wireless networks. This specification of the two layers (Physical & Media Access Control) is kown as WLAN or WIFI. Common protocols like the TCP/IP or ARP operate on top of these two layers.
Basic Service Set
A WLAN consists of a minimum of two communication partners, also called stations. These stations can communicate with each other using electro-magnetic waves, that have a scope of 20m – 300m. This communication area is known as Basic Service Set (BSS). In order to increase the scope of a wireless network, it is common to introduce access points into the network. These access points relay the traffic from stations and thereby increase the overall communication scope. Anyone in the scope of the Basic Service Set can listen to the traffic of the wirless network.
Packet Design
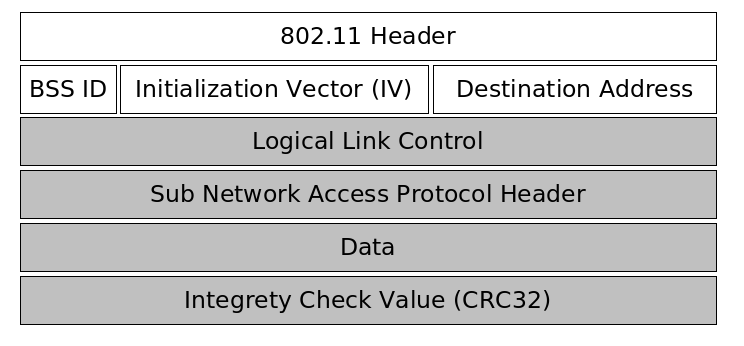
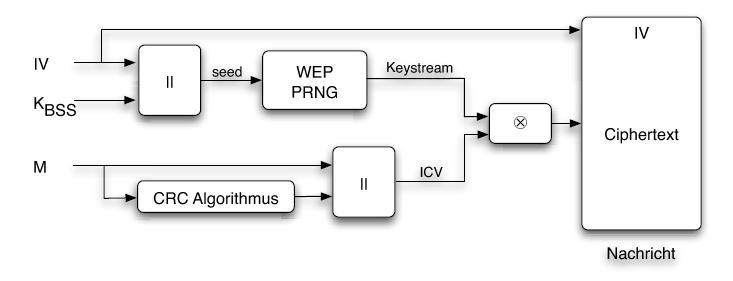
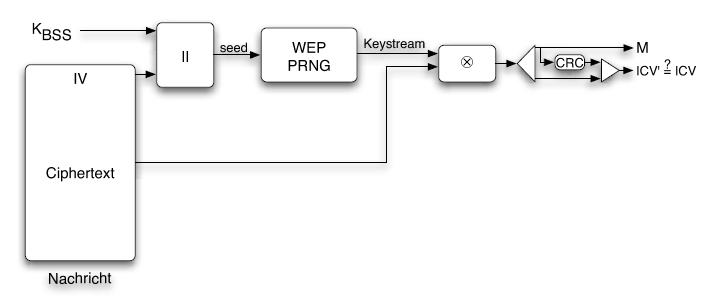
The first part of a packet is unencrypted and contains the 802.11 header, the basic service set identifier, an initialization vector chosen by the sender of the packet and the destination hardware address. The initialization vector is transmitted unencrypted because it is used along with a secret password to initialize a pseudo number generator. The receiver of the packet only knows the secret password, and must be able to initialize the pseudo random number generater with the same value the sender did.
The second part of the packet is encrypted and carries the data of the above protocols as well as an CRC32 integrety check value.
The following picture illustrates the design of WEP packet.
Packet Encryption & Decryption
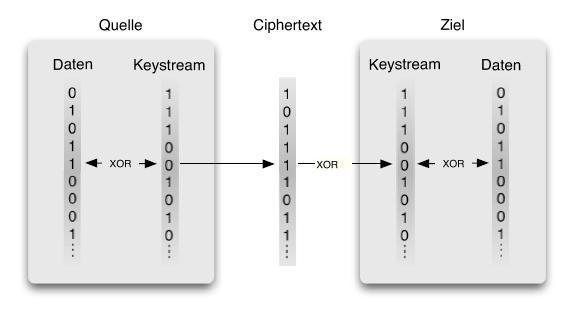
Because anyone can listen to the communication of a wireless network, the IEEE 802.11 includes a cryptographic method to secure the communication between stations and access points. This is done by sending encrypted packets between the communication partners. These packets should only be encryptable and decryptable by communication partners, that know the same secret password.