Distributed Denial of Service: Difference between revisions
No edit summary |
No edit summary |
||
| Line 4: | Line 4: | ||
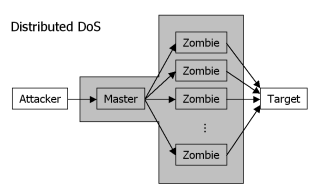
The attacker will exploit known, widespread vulnerabilities to install client software on as many systems as possible. Most of those systems will act as ''clients'' (or "zombies"), waiting for the command to begin a [[DoS]] attack. One or more systems though will act as ''masters'' that know the addresses of the ''clients'' and wait for a signal themselves. |
The attacker will exploit known, widespread vulnerabilities to install client software on as many systems as possible. Most of those systems will act as ''clients'' (or "zombies"), waiting for the command to begin a [[DoS]] attack. One or more systems though will act as ''masters'' that know the addresses of the ''clients'' and wait for a signal themselves. |
||
When the attack is to begin, the ''master(s)'' receive a message containing the target of the attack. They spread the message to the clients, which in turn begin to send packets to the target (depending on the type of the DoS attack). |
When the attack is to begin, the ''master(s)'' receive a message containing the target of the attack. They spread the message to the ''clients'', which in turn begin to send packets to the target (depending on the type of the DoS attack). |
||
In order to cover the anonymity of the attacker, communication between ''attacker'', ''hosts'' and ''clients'' often will use faked source addresses and encrypted communication. |
|||
Grouping the ''clients'' and let different groups attack at different times may help making the attack more efficient. |
|||
Some schemes common to [[Botnet|botnets]] are also adopted sometimes, like organizing the ''clients'' in a peer to peer network and using IRC as communication channel. |
|||
Revision as of 17:36, 14 November 2004
When conducting a Distributed Denial of Service attack (abbr. DDoS), a multitude of systems are used for a Denial of Service attack. This scheme is similar to a botnet. In fact, botnets are often used for DDoS attacks, but possess much more abilities.
The attacker will exploit known, widespread vulnerabilities to install client software on as many systems as possible. Most of those systems will act as clients (or "zombies"), waiting for the command to begin a DoS attack. One or more systems though will act as masters that know the addresses of the clients and wait for a signal themselves.
When the attack is to begin, the master(s) receive a message containing the target of the attack. They spread the message to the clients, which in turn begin to send packets to the target (depending on the type of the DoS attack).
In order to cover the anonymity of the attacker, communication between attacker, hosts and clients often will use faked source addresses and encrypted communication. Grouping the clients and let different groups attack at different times may help making the attack more efficient. Some schemes common to botnets are also adopted sometimes, like organizing the clients in a peer to peer network and using IRC as communication channel.